1,使用openssl生成证书,生成命令如下,其中:/C=CN(国家缩写)/ST=(省份)/L=(城市)/O=(组织名称):
openssl req -x509 -nodes -days 3650 -newkey rsa:2048 -subj "/C=CN/ST=ZheJiang/L=HangZhou/O=MJY" -keyout CA-private.key -out CA-certificate.crt -reqexts v3_req -extensions v3_ca
openssl genrsa -out private.key 2048
openssl req -new -key private.key -subj "/C=CN/ST=ZheJiang/L=HangZhou/O=MJY/CN=127.0.0.1" -sha256 -out private.csr
#最后的 CN=IP地址或域名2,生成ext文件:
#vim private.ext
#复制如下内容到private.ext文件中
[ req ]
default_bits = 1024
distinguished_name = req_distinguished_name
req_extensions = san
extensions = san
[ req_distinguished_name ]
countryName = CN
stateOrProvinceName = Definesys
localityName = Definesys
organizationName = Definesys
[SAN]
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = IP:127.0.0.13,生成CA证书
openssl x509 -req -days 3650 -in private.csr -CA CA-certificate.crt -CAkey CA-private.key -CAcreateserial -sha256 -out private.crt -extfile private.ext -extensions SAN4,复制证书至相应目录, nginx为例
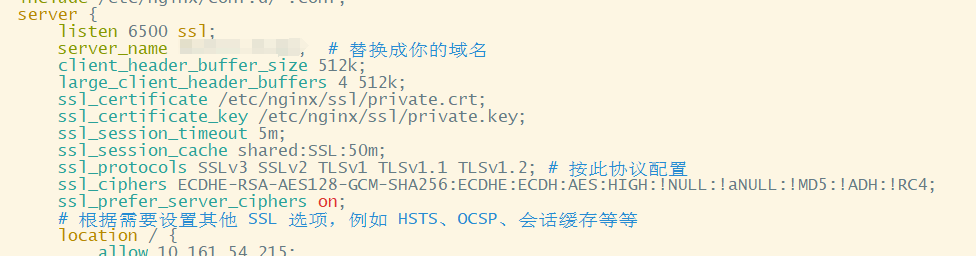
ssl_certificate /etc/nginx/ssl/private.crt;
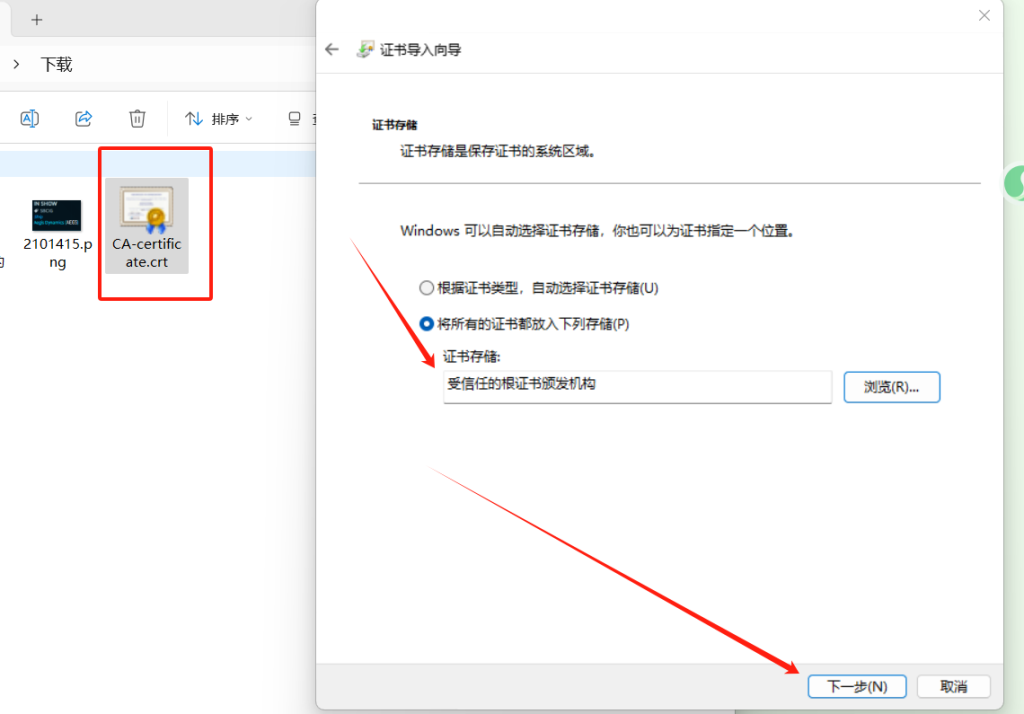
ssl_certificate_key /etc/nginx/ssl/private.key;5,将CA证书导入受信任的根目录中

No Comments